The Chinese time bomb
At Seculert, when we analyze a targeted attack, we are trying to help our customers understand the intention of the attackers, as we look how the attack evolves over time. In some cases, understanding the intention behind the attack requires attribution to a specific group or region.
For instance, with the Mahdi campaign, we were able to find that the attackers were fluent in Farsi and even used a Persian calendar in the communication with the C2 (Command & Control) server.
Two weeks ago, Mandiant revealed that multiple attacks throughout the recent years are presumably attributed to one group of attackers, unit 61398 in the Chinese PLA. Two days later, we discovered two different spear-phishing attacks which were using a fake Mandiant report to target Japanese and Chinese journalists.
Today, we would like to add additional interesting information in regards to the targeted attack against the Japanese.
When we analyzed the malware that was used in this targeted attack, using Seculert Swamp, we found that while the malware was communicating with legitimate Japanese websites, it still had an additional C2 domain in memory. The domain – expires.ddn.dynssl.com – which was registered using a free dynamic DNS service, resolves to a server located in Korea (IP address 218.53.110.203).
Interestingly enough, without the “expires”, the ddn.dynssl.com domain resolves to the IP address 123.234.29.35, which is a server located in Jinan, the capital of the Shandong province of China (See Figure 1). A region which is presumably linked to the “Google Aurora” and the “Shady RAT” operations, which are also mentioned in the Mandiant report (though attributed to different APT groups). Oh, the irony…
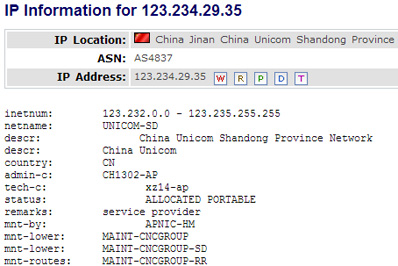
Figure 1: IP information of ddn.dynssl.com domain (Source: domaintools.com)
Further analysis of the malware revealed that, much like a time bomb, the malware is set to trigger only during a specific timeframe. Up till then, the malware will communicate with the legitimate Japanese websites, and only on Tuesday’s between 8am and 7pm (See Figure 2) will it start communicating with the real C2 server. At this point the malware will download and execute a new piece of malware, basically setting up the stage for a new phase of the targeted attack.

Figure 2: Time bomb malware code set to trigger on Tuesday between 8am and 7pm
Fortunately, the domain was suspended by the dynamic DNS service provider last Monday, a day before the time bomb was supposed to be triggered, therefore, the next phase of the attack did not commence.