High-risk Broadcom UPnP stack remote root vulnerability
Recently, DefenseCode researchers have uncovered a remote root access vulnerability in the default installation of Linksys routers. Further research revealed that the vulnerability is even more dangerous, since the same vulnerable firmware component is also used by numerous other router manufacturers.

The vulnerability is located within the wanipc and wanppp modules of the Broadcom UPnP stack, which is used by manufacturers that deliver routers based on the Broadcom chipset.
A variety of routers have their UPnP interface available over the WAN interface, so the vulnerability can also be exploited over the Internet. It seems that, at the moment, the only popular UPnP implementation not hit by the remote preauth security vulnerability is MiniUPnP.
The remote preauth format string vulnerability in the Broadcom UPnP stack can be exploited to write arbitrary values to an arbitrary memory address, and also to remotely read router memory. When exploited, it allows an unauthenticated attacker to execute arbitrary code under the root account.
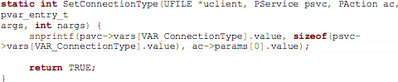
The vulnerability present in the SetConnectionType function of wanipc and wanppp modules can be reached with a single SOAP request that calls SetConnectionType function.
SetConnectionType:

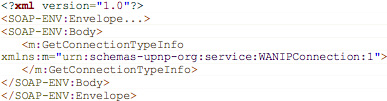
The format string output is available through a GetConnectionTypeInfo SOAP request as presented below.
GetConnectionTypeInfo:
The format string vulnerability is present because the user-input from the SOAP request is supplied as a format string argument to the snprintf() function in wanipc.c and wanpp.c. The vulnerable code lines are located in the following files and code lines:
/upnp/igd/wanipc.c:
/upnp/igd/wanppp.c:

Some of the manufacturers contacted regarding this vulnerability are:
- Broadcom
- Asus
- Cisco
- TP-Link
- Zyxel
- D-Link
- Netgear
- US Robotics.
At this time, it’s unclear how much it will take for patches to be released.