When it comes to breaches, time is the biggest challenge
A new SANS report includes results of a survey that polled 430 security and risk professionals from the SANS community, all working in private and public sector organizations ranging in size from 100 to more than 15,000 employees.
SANS community members polled in this survey are deeply involved in developing their organizations’ overall security strategies, choosing effective technologies and are on the front lines in the fight against attackers.
Survey findings provide key insights into understanding and improving data center and cloud security. Of note, 55 percent of respondents were dissatisfied with the length of time it takes them to contain and recover from attacks.
“When it comes to limiting damage and preventing data breaches, time continues to be the biggest challenge for security and risk professionals,” said SANS analyst Dave Shackleford. “Most respondents said they use traditional tools to monitor traffic between data centers and internal or external clouds, and are unhappy with the level of visibility and containment speeds they get. If our security stance is going to improve, we need better visibility, the ability to make configuration changes faster and to contain attacks more quickly.”
According to the survey, 59 percent of organizations are able to contain attacks within 24 hours, leaving many open to prolonged and increased damages as attacks spread laterally through data centers and clouds. Containment times reported by respondents included:
- 37% — up to 8 hours
- 21% — up to 24 hours
- 19% — less than a week
- 17% — more than a week.
The wide range of response times, according to the SANS report, may be the result of the inability of some traditional security tools to assist organizations in detecting and managing attack scenarios. According to the survey, between 75 and 96 percent of organizations are using traditional solutions in data centers, which include everything from firewalls to those that focus on detection and intrusion prevention such as IDS, IPS, IAM and anti-malware.
“Organizations should have controls that keep security in place regardless of where digital assets are located. That means looking beyond network perimeters by adding a focus on enacting policies and controls closer to application workloads and associated data flows distributed across data centers and clouds,” Shackleford said.
Survey results also show that organizations using legacy tools and strategies need to take steps to improve overall security and compliance. The addition of cloud computing and overall lack of solutions and methods available to address specific security challenges in these environments is also increasing risk.
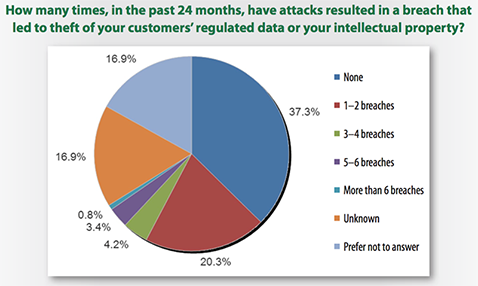
Traditional tools not stopping breaches – 44 percent of enterprises reporting breach information have had sensitive data accessed by attackers—these same respondents were among those using traditional security tools in their data centers and clouds; 28 percent of organizations have experienced up to six data breaches in the past 24 months. Tools in use by the respondent segment include everything from network firewalls (used by almost 100 percent of respondents) to IDS, IPS, IAM and anti-malware technologies.
Security losing ground in cloud, distributed computing game – 37 percent of organizations use distributed cloud and data center computing systems; 44 percent of respondents said their biggest challenge was that cloud providers don’t offer visibility needed to protect users and data; 19 percent say cloud providers don’t give them security support needed; and 49 percent have no formal cloud security strategy in place. Making matters worse is the lack of effective security controls available and in use. While 75–100 percent of respondents are using traditional tools in data centers, that number drops off to less than 35 percent in the cloud.